In this article we take a high level look at some of the Mobile Application Security Testing approaches. Test engineers need to use the most effective, fast and understandable environment for conducting the testing process and also to supplement it with a flexible infrastructure to support the implementation of full-scale testing in a situation where the frequency of updating the number of mobile devices and digital technologies is rapidly increasing.
Mobile Apps Industry – Opportunity and Demand
As per the CTT company, detailed report of 2016 implies: the profit increase of the mobile sector to 530 billion US dollars is expected at the end of 2020.
However, the rapid growth in demand for mobile gadgets involves not only analyzing how to use them but also requires significant financial costs to conduct an optimized procedure for testing the mobile apps.
According to ABI Research, the number of sales of tools, which allow manual analyzing the performance of mobile applications, has increased from 200 million to 850 million from 2012 to 2017.
It speaks volumes that the mobile development sphere with subsequent performance verification of its individual components is quite a demanded procedure, which makes a sense to consider the mobile applications testing processes more detailed, in particular, such a direction as the security check of the developed application.
Mobile Application Testing Process
Virtually all of the studies, which are conducted during the mobile application testing process, are directly or indirectly related to such actions:
- White box (test object whose features are known to the tester) + unit testing;
- Black box (test object whose device is unknown before the process of testing) + testing the visual performance of the mobile application;
- Verification of the established validation of the quality of service parameters (QoS, Quality of Service);
- Usability testing of the utility;
- Opportunities to connect the automation infrastructure for testing mobile technologies;
- Work with security systems.
If we consider the term “testing mobile programs in the security perspective” we can distinguish the fact that this term covers the verification of not only the developed application and the work with testing utilities specially created for the operation of another application, as well as a set of work to test mobile web applications.
In general terms, a mobile product testing is a set of test actions that are conducted in a strictly established sequence and guarantee the performance of all the functions declared in the technical documentation, fully meet the quality standards and also have the characteristic system features: mobility, usability, connectivity, logical consistency and, of course, security!
Specified requirements
Checking the mobile application efficiency is very different from the tests that are carried out when examining the classic software functionality. After all, in the first case, several original and unique requirements must be applied at once.
First of all, due to the fact that the mobile application must be correctly executed under any conditions at any time.
It is very important that the mobile product functions correctly on various platforms which use completely different OSs, the ratio of the screen size, as well as the technological characteristics of computing capacities, and, of course, the maximum indicators of the battery life.
Any mobile application should be “mobile” in everything: from the methods (channels) of information input to maintaining work with other multimedia systems and services.
So, the mobile product should work optimally in any heterogeneous network environment considering the trend of mobile services in a fairly wide range of wireless networks.
Core objectives and ongoing activities
It can be identified such groups of objectives and activities for optimal software testing services when taking into account the requirements for testing applications:
- Checking the functional part and system behavior allows QA to understand how the functions inside the system interact, connected APIs, external systems, as well as user interface complexes
- QoS checking means a work on testing the load on the system, checking its stability, throughput, and scalability
- Verification of interoperability is an analysis of the ability of the system to interact with various mobile devices and wireless networks
- Checking the degree of confidentiality and security means carrying out measures to verify the client authentication logic, device security, work session security, potential penetration capabilities, compliance with common security rules and the level of client data confidentiality
Types of mobile application security testing
The most common and important elements of conducting mobile security are the verification of such systems and components:
- Potentially unsafe storage of information
- Low data transmission protection threshold
- Weak authentication and authorization level
- Unsafe management and session management
Potentially unsafe storage of information
This problem has several important “sub-problems” as:
- Hardcoded and forgotten
- Incorrect files permissions
- SD Storage
- Logs
Let’s consider each component separately.
Hardcoded and forgotten
For example, we have an application for the Android operating system. As is well known, it comes in the form of a special apk file (original archive which contains resource and executable files).
Sometimes it’s enough just to go into resource files and you can find these elements which in theory should not be in the supplied product: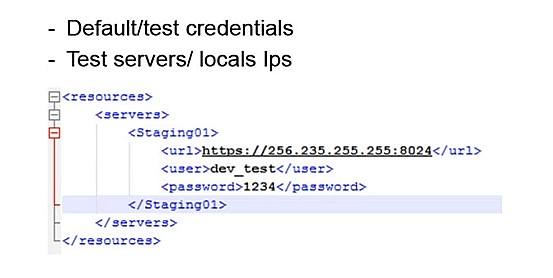
1. Incorrect file permissions
Here the main problem is that, as is known, any application has its own original UID – a specialized number (ID) by which it can be found on the network. It uses a fairly common principle – one application – one path. However, sometimes, the system needs to get its personalized access to the files in order to output some functions to the console. Then a completely different path is indicated and that is not good!
The example: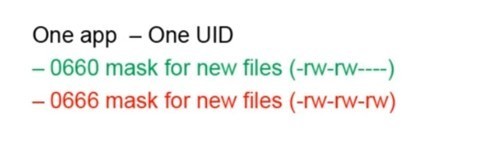
2. SD Storage
It’s no secret that the user data, that is on the SD card, can easily be used by other applications. They do not have such an intra-system protection.
Everything would be fine if the applications load simple photos or video on a memory card. Not at this time. There are utilities that “are able” to record to external media cookies or special authorization tokens. So, it is precisely this logic that should be avoided of, if possible.
3. Logs
Web developers try to use the process of logging (the logic is automatically recorded in the file environment of the smartphone) during a mobile product development very often.
The same about Android, it could easily configure the intra-system files so that the installed on the device application could request the android.permission.READ_LOGS function before the release of version 4.4.
The example: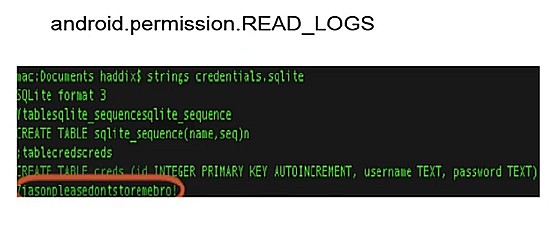
Summing up, the following recommendations can be noted:
- Try not to store data on the memory card
- Be sure to turn off the logging
- Customize rights, taking into account that a potential customer can use a smartphone with Root rights or with a jailbreak
- View the configuration files of your utility for forgotten data
Low data transmission protection threshold
This problem has several important “sub-problems” such as:
- No encryption was used
- Use of self-signed certificates
Encryption
In order to avoid problems with the encryption area, it is recommended:
- Check mobile application traffic
- Use certificates that have been signed by trusted centers
- Verify and prescribe access rights if you use content providers (content provider provide access to files or databases for other applications)
Weak authentication and authorization level
The given problem has several important “sub-problems” as:
- Anonymous work with the utility
- Use of clients with a low level of system privileges to obtain an accessible to all users’ information
- Weak and simple passwords
In this case protection methods should be as follows:
- Authentication in the application should be similar in the web version
- Local authentication must function through the cookie system after the client has been authorized in the server
- Anonymous access disable
- Introduction of the client rights verification
- Complex passwords
- Change of an anonymous customer to a registered one
- Switch between registered users
- Switch between clients with different access rights
An important recommendation for this case – the registration token should be removed on the server. All cookies should be invalid!
It is also possible to note such useful reference as for how to use user session in time slice, namely:
- No more than 15 minutes for an application with a high level of security
- About 30 minutes for applying an average level of security
- More than 1 hour for all others
In the end, it can be identified as a group of problems which prevent developers from creating the safest and most secure applications and software testing companies to test them:
- Test environment – As many reviews of developers say, the current mobile test environments are still very expensive and not understandable. Creating an optimized environment to test multiple applications on one site turns into a very long and complex process and constant operational updates of web platforms only aggravate the current situation. Ideally, the testing environment should consist of such components: unified support for different web platforms, a wide range of configurations taking into account the functions of the operational deployment, as well as parameters for the diversification of the required configurations;
- Automation – It is the processes of the security automated testing of the mobile utility that cause the greatest questions because there is no generally accepted standardization of the test environment for carrying out the corresponding checking The creation of emulating clouds, a set of commands for creating, deploying and managing applications that allow you to work with the internal filling of any developed application can be the way out of this situation.
As a result, it turns out that it is the testing environment for the security of mobile products that is the most vulnerable and up-to-date direction that should be developed everywhere and supplemented with new verification parameters and testing in order to minimize the number of bugs that are allowed in the product development.
Other popular articles:
- What are Security testing tools in software testing?
- What is Verification in software testing? or What is software verification?
- What is Validation in software testing? or What is software validation?
- What is Security testing in software testing?
- Mobile application development and testing checklist – 17 points to remember before developing an app
james moser says
informative content thanks for sharing